Multi-Path Room - Connect to an AWS VPC
This article explains how to connect an AWS VPC (Virtual Private Cloud), also referred to as an Amazon VPC, to a Tehama Multi-Path Room.
Overview
What is a Tehama Multi-Path Room?
A Multi-Path Room is a short way of referring to a Tehama Room that has network access type "Multi-Path". This network access type is capable of securely connecting to networks through IPSec. Multi-Path Rooms support many such connections.
See the Multi-Path Room Connectivity User Guide for more details about Multi-Path Rooms.
Currently, only Standard Rooms support the "Multi-Path" network access type. Domain Join Rooms do not, as yet, support it.
Find out what your Room's network access type is from the Room's connection page. See section View a Room's network access setting in the Room/Desktop Connectivity - Types, Status and Settings guide for details.
What is an AWS VPC?
An AWS VPC is a cloud-based private network hosted in Amazon's AWS cloud. See the Amazon article What is Amazon VPC? for more information.
Assumptions
- You have a Tehama organization and are an Admin or Org Manager user in that organization.
- You have an AWS VPC that contains company resources, data, etc., that you want to access, securely, from a Tehama Room.
The process to connect an AWS VPC is divided into three parts:
- Create a Tehama Multi-Path Room
(optional - you can also make a connection to an existing Multi-Path Room.) - Add and Configure a New Connection
- Check the Status of the Connection
Create a Tehama Multi-Path Room
If you want to connect your AWS VPC to one of your existing Tehama Multi-Path Rooms, simply note the Room's name and skip to the next step.
Either:
- Create a new Tehama Multi-Path Room by following the steps found in the Getting Started with Tehama Room Creation guide, under section 'Create and connect a Standard Room', selecting 'Multi-Path' as the Room's Network Access type.
or
- Convert one of your existing Rooms with 'Tehama Gateway' or 'Internet-Only' network access to use 'Multi-Path' network access, by following the steps found in the Room/Desktop Connectivity - Types, Status and Settings guide, under section 'Change a Room's Network Access setting'.
Take note of your Multi-Path Room's name, for use in the creation of your connection.
Information gathered in this step:
- The name of your Multi-Path Room.
Add and Configure a New Connection
Add and configure a connection to your AWS VPC from your Tehama Multi-Path Room as follows:
First, gather some information about your AWS VPC.
Next, create and configure an AWS Site-to-Site VPN connection between your VPC and your Multi-Path Room.
- B) AWS - Create a VPN Gateway
- C) AWS - Attach Your VPN Gateway to Your VPC
- D) Tehama - Begin Creating a Connection in Your Multi-Path Room
- E) AWS - Create and Configure a Site-to-Site VPN Connection
- F) Tehama - Complete the Connection in Your Multi-Path Room
Next, configure your VPC routing to use the connection to pass traffic between them through the connection.
- G) AWS - Configure the Route within the VPC
- H) AWS - Add Static Route to Multi-Path Room subnet, if not already added
Finally, update any AWS security groups you may have defined in your VPC, and your Multi-Path Room's firewall rules (and optionally its DNS Filtering) to allow access to resources in your VPC from your Room's Tehama Desktops.
Let's get started with step A.
A) Find Your VPC Info
This step looks up your VPC in the AWS management console to find the information needed from it to connect your VPC to your Multi-Path Room. You should already know either your VPC's name or its subnet or its ID. You will need to know at least one of them before you begin. (Ask your IT dept for assistance, if you do not know either of them.)
Required information for this step:
- Your AWS account login info.
- Identifying data for your VPC, e.g.: name, subnet and/or ID.
- Your VPC's region, (optional if you know the ID).
- Open a new browser tab, (referred to as the AWS browser tab).
- Log in to your AWS account, in the AWS management console.
- Select the region in which your VPC resides, if you know it, in the dropdown list of regions located at the top right of the page. If you do not know the region, then look in each region until you find your VPC. The ID is globally unique.
- Navigate to the VPC interface. Go to VPC → VIRTUAL PRIVATE CLOUD → Your VPCs.
- Click on Services, at the top navigation bar, to the left of the search field.
- Select Networking & Content Delivery, in the side navigation bar.
- Click on VPC, from the list of offerings in the centre pane.
- Open the VIRTUAL PRIVATE CLOUD sub-menu in the side navigation bar.
- Select Your VPCs from the sub-menu. You will see a list of your VPCs.
- Find the entry for your VPC in the list (identify by name or subnet or ID - ask your IT dept for assistance if you do not know any of these).
- Take note of your VPC's name (value in the Name field).
- Take note of your VPC's subnet (value in the IPv4 CIDR field).
- Take note of your VPC's region (value at the top right of the page).
Information gathered/confirmed in this step:
- Your VPC's name.
- Your VPC's subnet.
- Your VPC's region.
B) Create a VPN Gateway
The Site-to-Site VPN connection we are going to create, needs a VPN Gateway to target in your VPC. This step creates one.
Required information for this step:
- Your VPC's region, from step A.
- A meaningful name for your new VPN Gateway.
- Continue in the AWS browser tab, where you left off in step A.
- Verify that your selected region is still the same region in which your VPC resides; see value from step A.
- Navigate to the Virtual Private Gateway (VPG) interface. Go to VPC → VIRTUAL PRIVATE NETWORK (VPN) → Virtual Private Gateways.
- Click on Services, at the top navigation bar, to the left of the search field.
- Select Networking & Content Delivery, in the side navigation bar.
- Click on VPC, from the list of offerings in the centre pane.
- Open the VIRTUAL PRIVATE NETWORK (VPN) sub-menu in the side navigation bar.
- Select Virtual Private Gateways from the sub-menu. You will see the VPG interface page, with a list of all your VPGs (VPN Gateways).
- Click on the Create Virtual Private Gateway button. You will see a form to create a new VPG (VPN Gateway).
- Fill out the form as follows:
- Name tag - enter a name for your new VPN Gateway. This will create a Name tag for this new object.
- Leave the ASN field on the default selection, which is the default Amazon ASN.
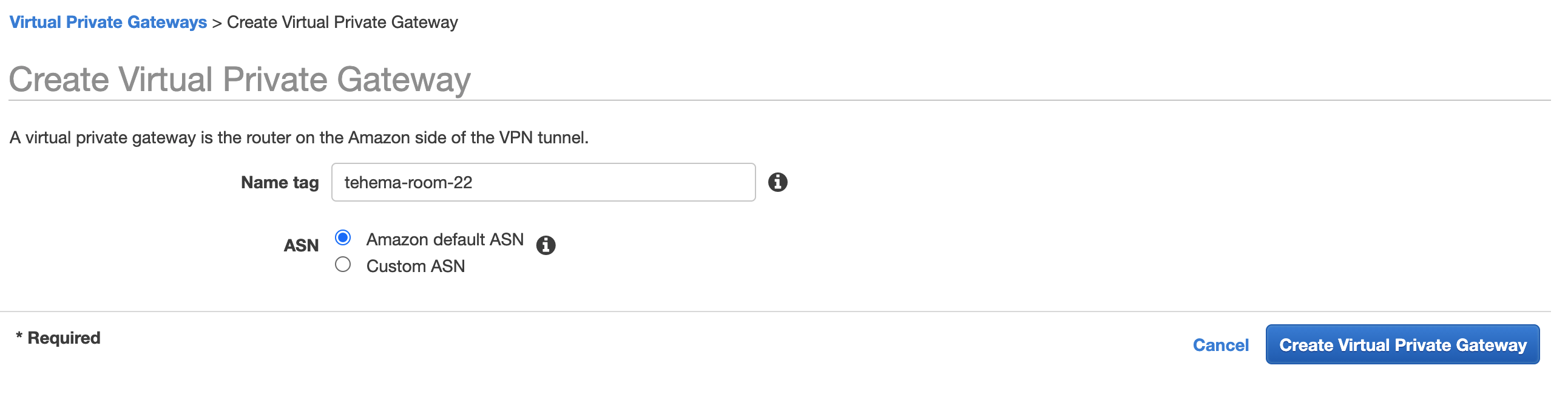
- Click the Create Virtual Private Gateway button on the form. You will be returned to the VPG interface page.
- Select your new VPN Gateway from the list on the interface page (you can identify it by the Name tag).
- Take note of your new VPN Gateway's ID.
Information gathered in this step:
- Your new VPN Gateway's ID.
C) Attach Your VPN Gateway to Your VPC
This step attaches your new VPN Gateway to your VPC.
Required information for this step:
- Your VPC's ID, from step A.
- Continue in the AWS browser tab, where you left off in step B.
- Click Actions to see the action menu items.
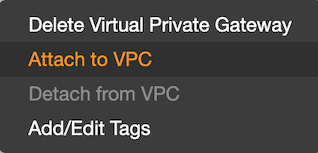
- Select "Attach to VPC". You will see a form asking you to select a VPC.
- Select your VPC (identify by name, from step A).
- Click "Yes, Attach".
Leave this browser tab open. You will return to it in step E.
Information gathered in this step:
- N/A.
D) Begin Creating a Connection in Your Multi-Path Room
In this step, we begin the creation of a new connection in your Multi-Path Room, to generate the pre-shared key for the connection. This key is needed for the next step, in AWS.
Required information for this step:
- Your Tehama corporate portal login info.
- Your Multi-Path Room's name.
- Open a new browser tab, (referred to as the Tehama browser tab).
- Log in to the Tehama Web UI.
- Click on the ROOMS tab.
- Click on the name of the Multi-Path Room you want to connect to your AWS VPC. You will see the page for the Room.
- Click on the Room's CONNECTION tab, if you are not already on this tab.
- Click the ADD CONNECTION button. You will see the form for creating a new connection.

- Copy the Pre-shared key value.
- Copy the Room IP value.
- Copy the Room Subnet value.
Leave this browser tab open. You will return to it in step G to complete the creation of your new connection.
Note: Each time you generate a new connection with the ADD CONNECTION button, you generate a new pre-shared key value. If you accidentally close the new connection form you created here before completing the connection in step G but after creating your site-to-site VPN connection in step F, you will need to re-create your site-to-site VPN connection with the new pre-shared key value you will get on the new connection form, when you click the ADD CONNECTION button again.
Information gathered in this step:
- Your Multi-Path Room's new connection's pre-shared key.
- Your Multi-Path Room's Room IP.
- Your Multi-Path Room's Room subnet.
E) Create and Configure a Site-to-Site VPN Connection
This step creates and configures a Site-to-Site VPN Connection between your VPC (targeting the new VPN Gateway you created and attached to the VPC in step B and step C) and your Multi-Path Room.
Required information for this step:
- A meaningful name for your new site-to-site VPN connection.
- Your new VPN Gateway's ID, from step B.
- Your Multi-Path Room's Room IP, from step D.
- Your Multi-Path Room's Room subnet, from step D.
- Your Multi-Path Room's new connection's pre-shared key, from step D.
- Your VPC's subnet, from step A.
- Return to the AWS browser tab, where you left off in step C.
- Navigate to the Site-to-Site VPN Connections interface. Go to VPC → VIRTUAL PRIVATE NETWORK (VPN) → Site-to-Site VPN Connections.
- Click on Services, at the top navigation bar, to the left of the search field.
- Select Networking & Content Delivery, in the side navigation bar.
- Click on VPC, from the list of offerings in the centre pane.
- Open the VIRTUAL PRIVATE NETWORK (VPN) sub-menu in the side navigation bar.
- Select Site-to-Site VPN Connections from the sub-menu. You will see the Site-to-Site VPN interface page, with a list of all your VPNs.
- Click the Create VPN Connection button. You will see the Create VPN Connection form.
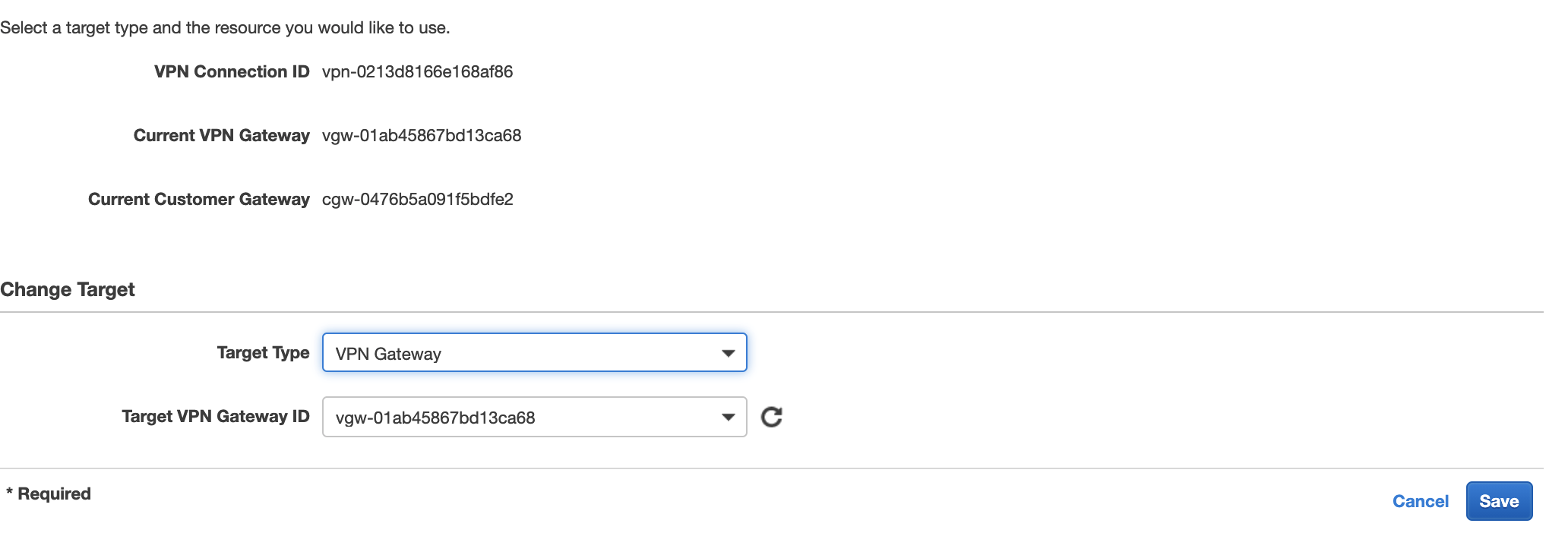
- Configure the Name and Target in the Create VPN Connection form:
- Name - enter a meaningful name for this new VPN connection.
- Target Type - select target type "VPN Gateway".
- Target VPN Gateway ID - enter the ID for the VPN Gateway, that you created in step B.
- Click the Save button. The Create VPN Connection form will expand, populated with values for your VPN Gateway.
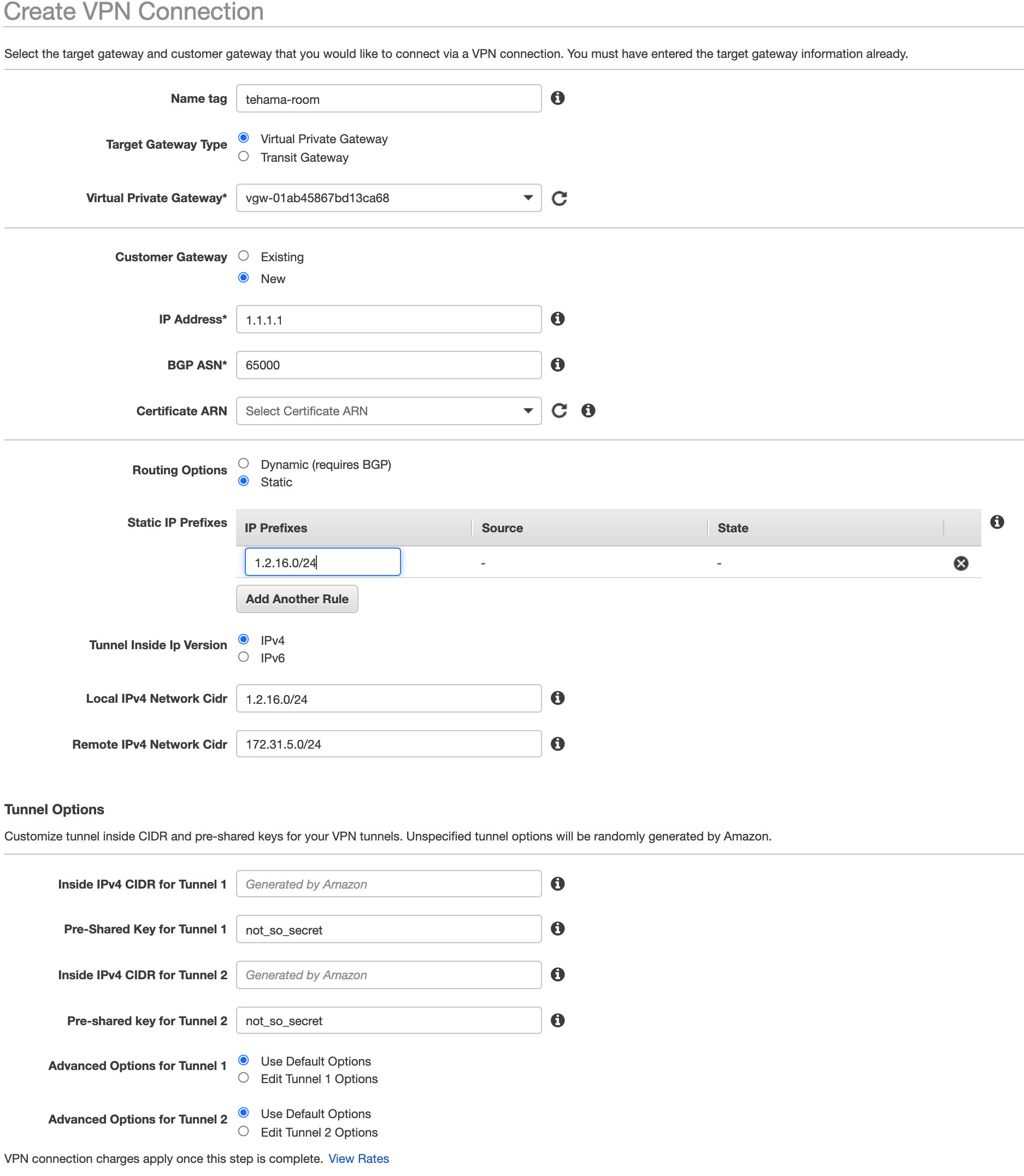
- Configure the Customer Gateway in the Create VPN Connection form:
- Customer Gateway - select “New”.
- IP address - enter your Multi-Path Room's Room IP, from step D.
- Configure the Routing Options in the Create VPN Connection form:
- Routing Options - select “Static”.
- Static IP Prefixes - enter your Multi-Path Room's Room subnet, from step D.
- Local IPv4 Network Cidr - enter your Multi-Path Room's Room subnet, from step D.
- Remote IPv5 Network Cidr - enter your AWS VPC's subnet, from step A.
- Configure the Tunnel Options (Tunnel 1) in the Create VPN Connection form:
- Under Tunnel Options, for Pre-shared key - enter your Multi-Path Room's new connection's pre-shared key, from step D.
- Click Edit Tunnel 1 options to expand the advanced options.
- Ensure Startup Action is set to Start for Tunnel 1.
- Configure for Tunnel Options (Tunnel 2) in the Create VPN Connection form:
- Under Tunnel Options, for Pre-shared key - enter your Multi-Path Room's new connection's pre-shared key, from step D.
- Click Edit Tunnel 2 options to expand the advanced options.
- Ensure Startup Action is set to Start for Tunnel 2.
This image shows the settings for Tunnel 1. Tunnel 2 will be similar.
- Click on Create VPN Connection on the bottom right to complete the connection.
- Go to the tunnel details of this new connection.
- Copy the Outside IP Address for one of the tunnels, to use as your VPC's public IP address in step F.
Information gathered in this step:
- Your new site-to-site VPN connection's name.
- Your VPC's public IP address (the new site-to-site VPN connection's Outside IP Address, retrieved from one of its tunnels).
F) Complete the Connection in Your Multi-Path Room
This step completes the creation of the new connection in your Multi-Path Room.
Required information for this step:
- Your VPC's subnet, from step A.
- Your VPC's public IP address (the new site-to-site VPN connection's Outside IP Address, retrieved from one of its tunnels), from step E.
- A meaningful name for your new connection.
- A description for your new connection.
- Return to the Tehama browser tab, where you left off in step D. You should see the new connection form that you opened in that step.
Note: Each time you generate a new connection with the ADD CONNECTION button, you generate a new pre-shared key value. If you accidentally closed the new connection form you created in step D and need to do it again, you will need to re-create your site-to-site connection with the new pre-shared key value. - In the new connection form:
- Name - enter a meaningful name for your new connection.
- Description (optional) - enter a description for your new connection.
- Target Subnet - enter your AWS VPC subnet, from step A.
The form allows you to enter more than one target subnet. Click on + Add more to bring up additional target subnet fields. - Public IP Address - enter your VPC's public IP address (the Outside IP Address from one of the two tunnels in the new Site-to-Site VPN), from step E.
- Click CONNECT.
Information gathered in this step:
- The name of your new connection in your Multi-Path Room.
G) Configure the Route within the VPC
Now you can begin the process of configuring your VPC routing to use the new VPN connection to pass traffic between the VPC and your Multi-Path Room. This step adds a route between your Multi-Path Room and the VPN's target VPN Gateway.
Required information for this step:
- Your VPC's ID or name, from step A.
- Your new VPN Gateway's ID, from step B.
- Your Multi-Path Room's Room subnet, from step D.
- Return to the AWS browser tab, where you left off in step E.
- Navigate to VPC → Route Tables. Go to VPC → VIRTUAL PRIVATE CLOUD → Route Tables.
- Click on Services, at the top navigation bar, to the left of the search field.
- Select Networking & Content Delivery, in the side navigation bar.
- Click on VPC, from the list of offerings in the centre pane.
- Open the VIRTUAL PRIVATE CLOUD sub-menu in the side navigation bar.
- Select Route Tables from the sub-menu. You will see the Route Tables interface page, with a list of all the Route Tables that exist.
- Select the route table for your VPC.
- Open the Routes tab. You will see the routes for your VPC.
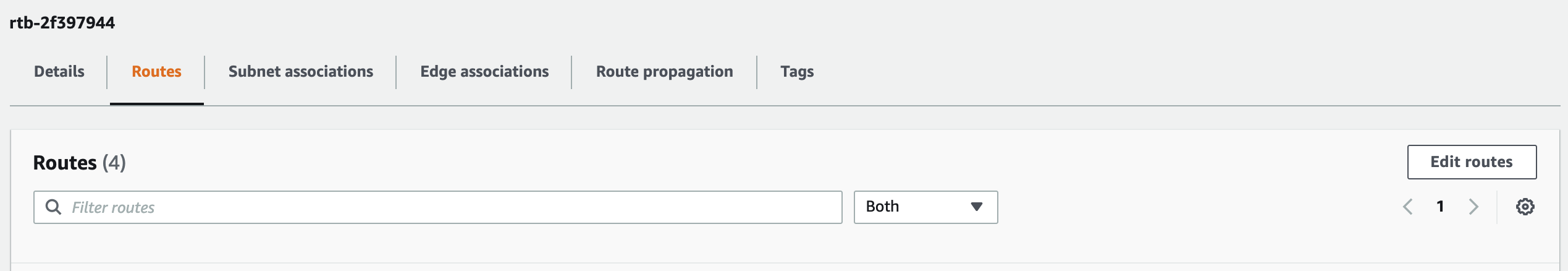
- Click Edit Routes. The route edit page will appear.
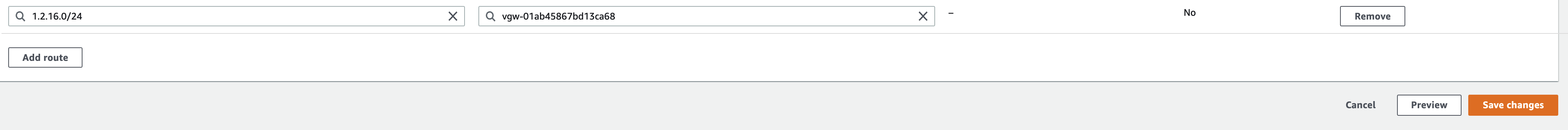
- On the route edit page, click Add route. The form to add a route will appear.
- Fill in the route information:
- Destination - enter your Multi-Path Room Subnet, from step D.
- Target - select the VPN Gateway you created in step B.
- Click Save routes.
- Back on the route edit page, click Save Changes.
Information gathered in this step:
- N/A.
H) Add Static Route to Multi-Path Room subnet
This step ensures that the route to your Multi-Path Room exists in your new Site-to-Site VPN connection.
Required information for this step:
- Your new site-to-site VPN connection's name, from step E.
- Your Multi-Path Room's Room subnet, from step D.
- Continue in the AWS browser tab, where you left off in step G.
- Navigate to the Site-to-Site VPN Connections interface. Go to VPC → VIRTUAL PRIVATE NETWORK (VPN) → Site-to-Site VPN Connections.
- Click on Services, at the top navigation bar, to the left of the search field.
- Select Networking & Content Delivery, in the side navigation bar.
- Click on VPC, from the list of offerings in the centre pane.
- Open the VIRTUAL PRIVATE NETWORK (VPN) sub-menu in the side navigation bar.
- Select Site-to-Site VPN Connections from the sub-menu. You will see the Site-to-Site VPN interface page, with a list of all your VPNs.
- Select the new Site-to-Site VPN, by name, you created in step E.
- Go to the Static Routes tab.
- Ensure there is a route to your Multi-Path Room. (Your Multi-Path Room's Room subnet value, from step D should be in the list of IP Prefixes.)
- If there is not such a route, then:
- Click Edit.

- Click Add Another Rule.
- Add your Multi-Path Room's Room subnet value to the prefixes.
- Click Save.
- Click Edit.
Information gathered in this step:
- N/A.
I) Update Security Groups
This second last step is to add your Multi-Path Room's Room subnet to any Security Groups you may have within your VPC for resources that you want your Room's Tehama Desktops to be able to access.
For each applicable Security Group:
- Continue in the AWS browser tab, where you left off in step H.
- Navigate to the Security Groups interface. Go to EC2 → Network & Security -> Security Groups.
- Click on Services, at the top navigation bar, to the left of the search field.
- Select Compute, in the side navigation bar.
- Click on EC2, from the list of offerings in the centre pane.
- Open the Network & Security sub-menu in the side navigation bar.
- Select Security Groups from the sub-menu. You will see the Security Groups interface page, with a list of all your Security Groups.
- Select the security group for the resource you wish to make accessible.
- Open the Actions menu.
- Select Edit inbound rules or Edit outbound rules, depending on what you want to allow.
- For Destination - choose Custom and enter your Multi-Path Room's Room subnet, from step D.
- Click Preview changes, then Confirm.
J) Update Firewall Rules/DNS Filtering
Finally, this last step is to update your Multi-Path Room's firewall rules, and optionally its DNS Filtering, to allow access to resources within your AWS VPC.
If you wish to completely open access to everything in your AWS VPC, add custom firewall rules to your Multi-Path Room allowing access to the entire subnet for your AWS VPC. Otherwise, add more granular rules.
See instructions on how to add firewall rules in section Add Custom Firewall Rule in the Firewall Rules User Guide.
You can optionally add an extra layer of access control on top of firewall rules through the Room's DNS Filtering feature. See the DNS Filtering guide for more details.
Check the Status of the Connection
Check the Status of the AWS VPN connection you set up between your AWS VPC and your Multi-Path Room.
Check connection status in Tehama
Required information:
- Your Tehama corporate portal login info.
- Your Multi-Path Room's name.
- The name of your new connection in your Multi-Path Room, from step F.
- Your VPC's public IP address (the new site-to-site VPN connection's Outside IP Address, retrieved from one of its tunnels) from step E.
- Open a new browser tab.
- Log in to the Tehama Web UI.
- Click on the ROOMS tab.
- Click on the name of the Multi-Path Room that you connected to your AWS VPC. You will see the interface page for the Room.
- Click on the Room's CONNECTION tab, if you are not already on this tab.
- Find the connection in the connection table (identify by name, from step F, or by your VPC's public IP address value, which is set to the Outside IP Address of one of the two tunnels in the site-to-site VPN, from step E).
- Verify that the connection status is green.
Check connection status in AWS
Required information for this step:
- Your AWS account login info.
- Your VPC's region, from step A.
- Your Site-to-Site VPN Connection's name, from step E.
- Log in to your AWS account.
- Select the region in which your VPC resides.
This is done through the dropdown list of regions located at the top right of the page. - Navigate to the Site-to-Site VPN Connections interface. Go to VPC → VIRTUAL PRIVATE NETWORK (VPN) → Site-to-Site VPN Connections.
- Click on Services, at the top navigation bar, to the left of the search field.
- Select Networking & Content Delivery, in the side navigation bar.
- Click on VPC, from the list of offerings in the centre pane.
- Open the VIRTUAL PRIVATE NETWORK (VPN) sub-menu in the side navigation bar.
- Select Site-to-Site VPN Connections from the sub-menu. You will see the Site-to-Site VPN interface page, with a list of all your VPNs.
- Select the new Site-to-Site VPN, by name, you created in step E.
- Click on the Tunnel Details tab.
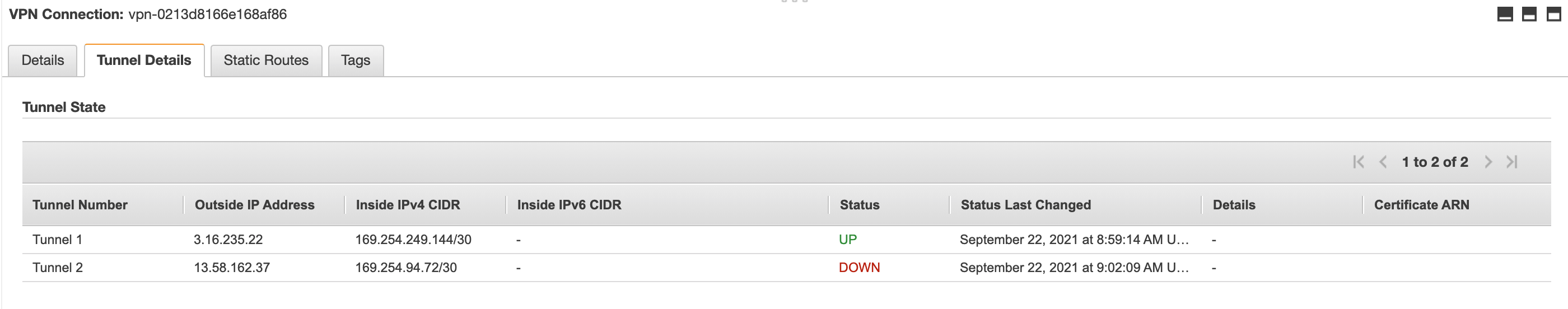
- Verify that everything is working:
- If everything is working, you’ll see one tunnel UP, and the other one DOWN. Only one will be active at a time.