SSO Centrify Setup
The following instructions set up an identity provider in Centrify.
Introduction
Centrify is a Single Sign-On (SSO) Provider and application portal that supports SAML 2.0, Secure Web Authentication and OpenID Connect. Tehama can be integrated with Centrify through SAML 2.0 and presented as a managed application alongside other Centrify integrated applications.
Once enabled, authentication to Tehama must be made through Centrify - local authentication through https://app.tehama.io is no longer possible except by using the Tehama Org Admin account. Centrify/Tehama Integration is limited to authentication only.
User accounts are required for both Centrify and Tehama. Both accounts must be configured with the same email address for SSO to work, and the user must accept the Tehama Welcome email before they will be able to launch a connection via Centrify SSO.
Integration Summary
Integration with Centrify SSO is a four-step process as follows.
- Obtain initial configuration settings from Tehama
- Create an application in Centrify
- Obtain the required Federation Metadata XML from Centrify
- Enter it back into Tehama
Prerequisites for Centrify Integration
- A Tehama Account with Org Admin privileges
- A Centrify account with Application Management privileges (i.e., System Administrator or a custom role with Application Management privileges)
Setup Time - 10 minutes
Create a connected application
Login to Tehama using the Org Admin Account and click on the ORGANIZATION tab in the navigation bar.
Select the AUTHENTICATION tab.
Check "Enable SAML Single-Sign on".

Make a note of the Entity ID and Callback URL (Assertion Consumer Service URL) values.
Open a second browser tab, sign in to your Centrify Account, and switch to the Admin Portal.
Select Apps from the top level menu.
Select Add Web Apps and open the Custom apps tab.
Scroll down the list of app templates until you find the SAML app and click on Add.
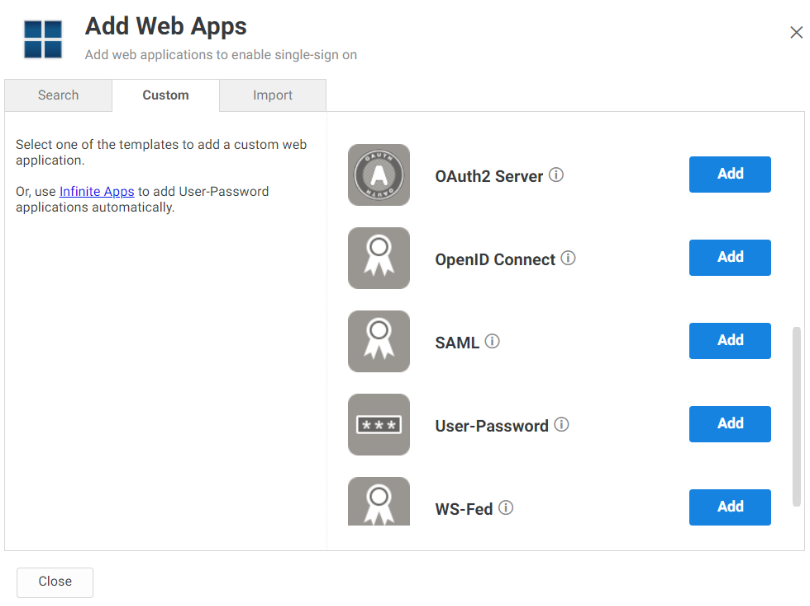
Confirm the selection then close the Add Web Apps window and the SAML app configuration screen will be displayed.
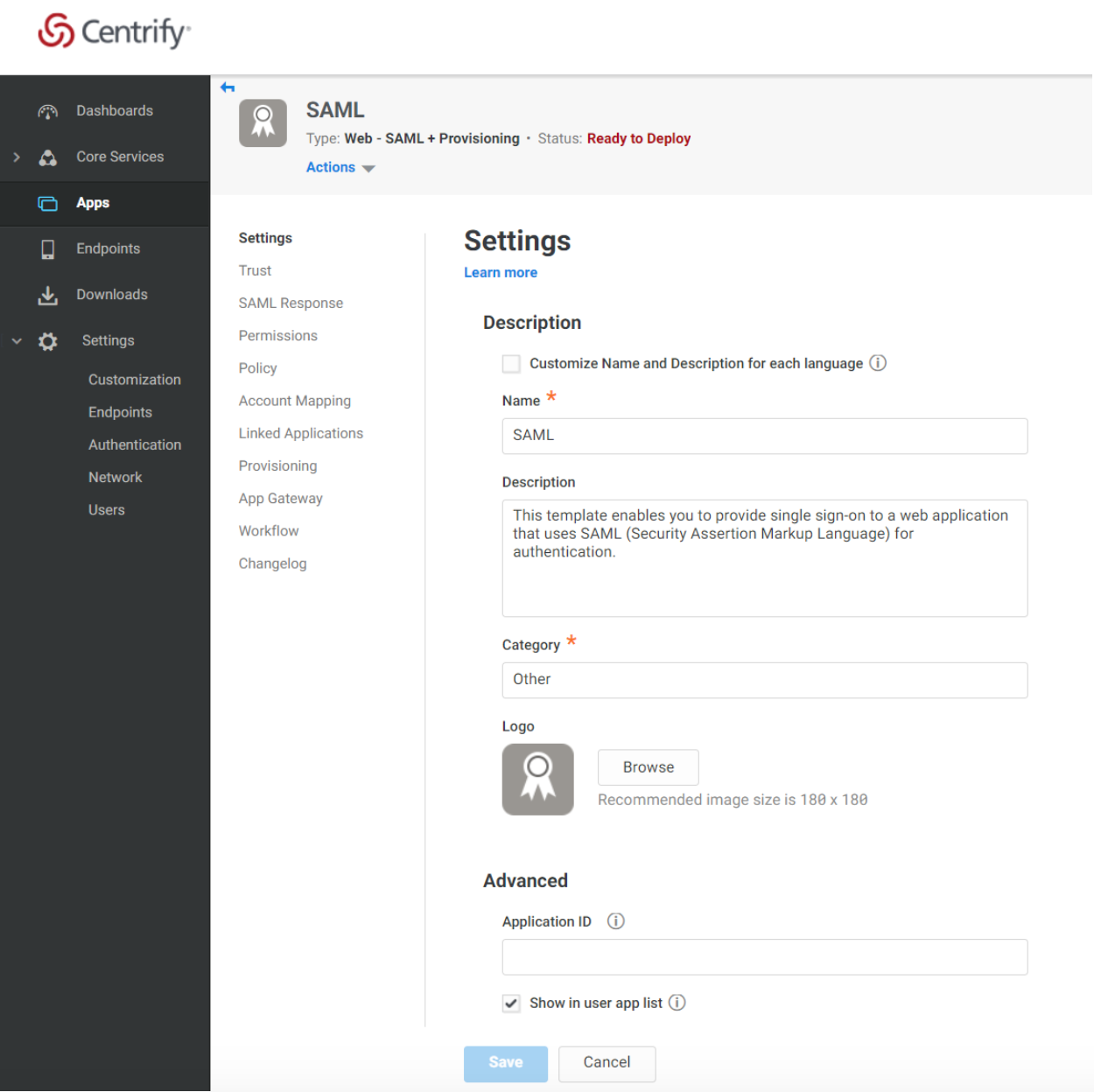
Provide an appropriate App name, description, and corresponding logo.
You may download and save a copy of this image to use as the logo if you wish:

Select Trust from the Customization Menu.
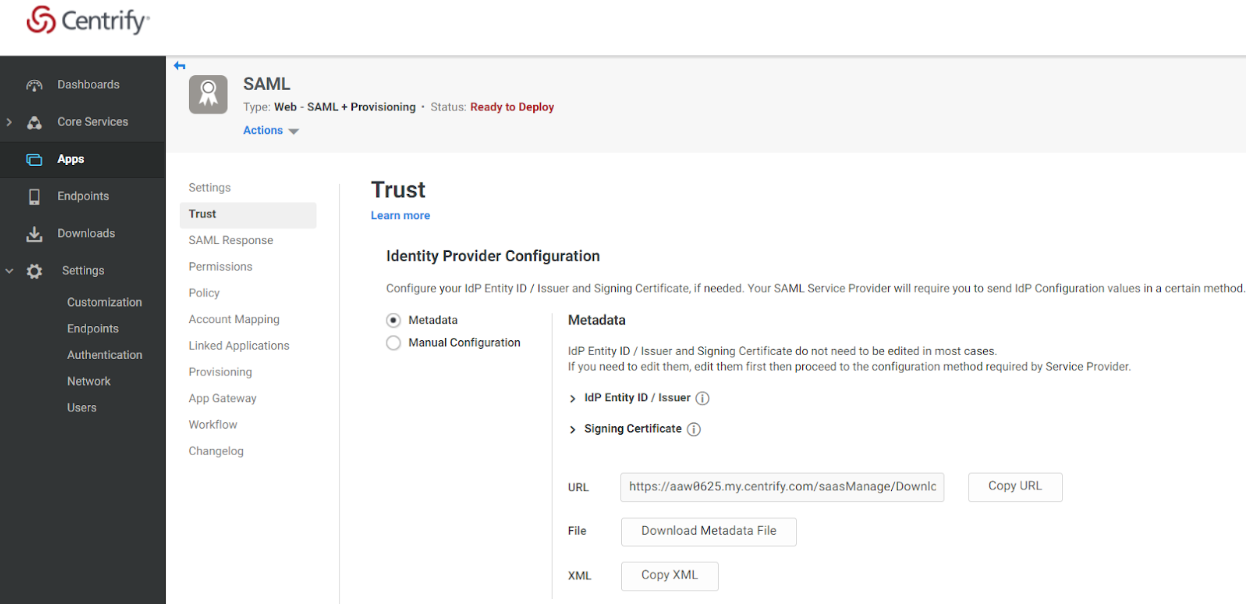
In the Identity Provider Configuration section, select the Metadata radio button, and select Copy XML.
Paste the XML data into Notepad or your preferred text editor, and perform a global search and replace to replace any “&” characters with “&” if present.
Scroll down to the Service Provider Configuration settings section of the page and select the Manual Configuration radio button.
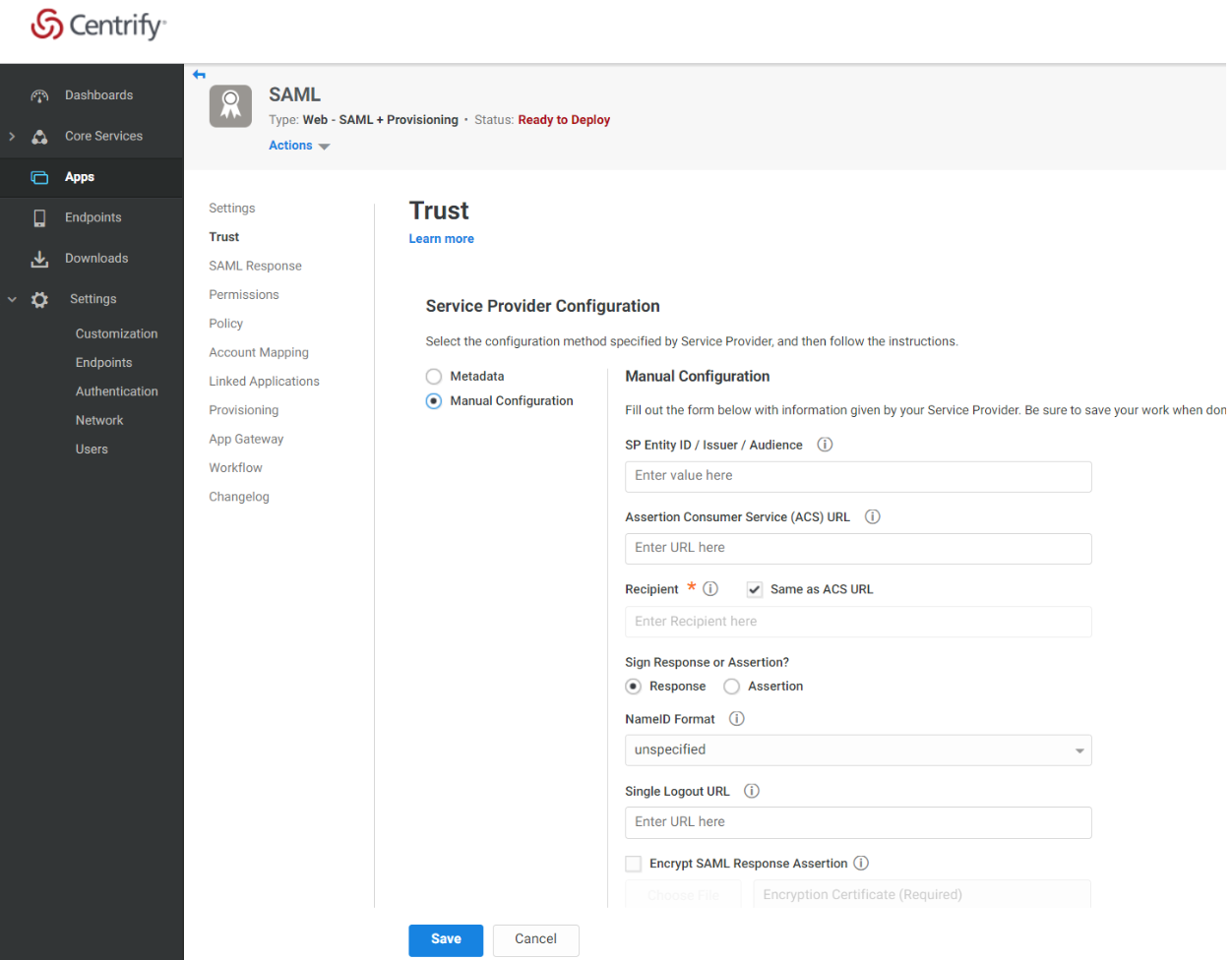
Copy the Entity ID from the AUTHENTICATION METHOD section of the Tehama Web UI's Authentication page and paste it into the SP Entity ID / Issuer / Audience field.
Copy the Callback URL (Assertion Consumer Service URL) from the AUTHENTICATION METHOD section of the Tehama Web UI's Authentication page and paste it into the Assertion Consumer Service (ACS) URL field.
Leave all other fields at their default values and click Save.
Select Permissions from the Customization Menu and assign the app to the required authorized users, and click Save to deploy the application. Optionally perform any additional application management tasks in line with your organization’s requirements.
Return to the Tehama Web UI and enable SSO by clicking on the checkbox to Enable SAML Single-Sign On (if not already enabled).
Copy the edited XML metadata from Notepad and paste it into the Federation Metadata XML box.

and click SAVE.
Now that you have completed this step, each existing team member in your organization will receive an email inviting them to configure their SSO login by clicking on the provided link, CONFIGURE SSO LOGIN, and to follow the instructions.
Each subsequently added team member will receive the same email and must also configure their SSO login by clicking on the provided link.
Configuration is now complete.